
by admin | Jul 3, 2025 | Uncategorized
In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual currency investment scam websites reported to the FBI. But a new report finds the accused continues to operate a slew of established...

by admin | Jun 30, 2025 | Uncategorized
Agents with the Federal Bureau of Investigation (FBI) briefed Capitol Hill staff recently on hardening the security of their mobile devices, after a contacts list stolen from the personal phone of the White House Chief of Staff Susie Wiles was reportedly used to fuel...
by admin | Jun 12, 2025 | Uncategorized
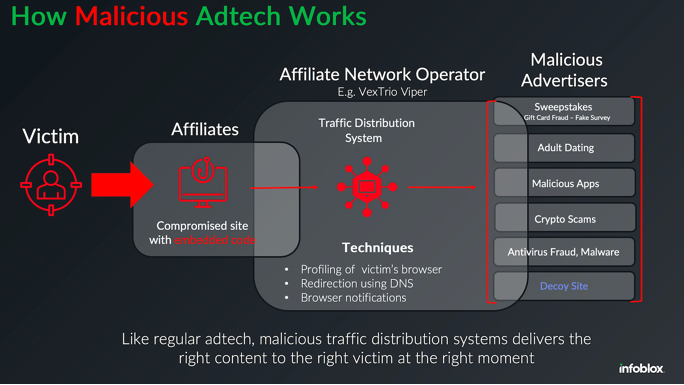
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising technology that powers a sprawling ecosystem of online hucksters...
by admin | Apr 30, 2015 | Uncategorized
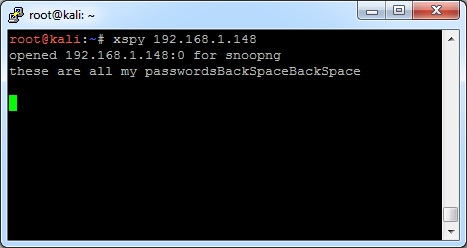
I’ve posted about open X11 servers before, including keylogging and grabbing an image of the desktop. Today I just want to add a couple other tools to the toolbelt. To learn more about X11, see the other posts as they describe it in better detail. Setup Your Testbed...
by admin | Apr 23, 2015 | Uncategorized
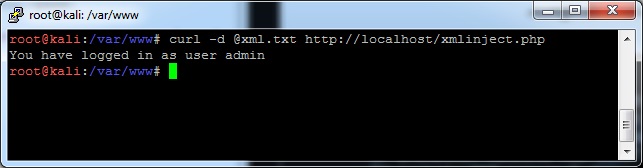
Within XML, there is a way to inject an external file. For a long time, automatic XML parsers (using libxml2 in the backend) had this enabled by default. So when XML is used as a means to format and pass data around, the website is very likely vulnerable. XML is...





